The Secure Shell Protocol (SSH) is a cryptographic network protocol for operating network services securely over an unsecured network. Its most notable applications are remote login and command-line execution.
What is SSH?
SSH applications are based on a client–server architecture, connecting an SSH client instance with an SSH server. SSH operates as a layered protocol suite comprising three principal hierarchical components: the transport layer provides server authentication, confidentiality, and integrity; the user authentication protocol validates the user to the server; and the connection protocol multiplexes the encrypted tunnel into multiple logical communication channels.
What SSH command ?
The ssh command is used to securely log into a remote machine and execute commands on that machine. The basic syntax of the command is “ssh user@severip -p”, where user is the username on the remote machine and host is the address or hostname of the remote machine.
SSH command.
| ls | List files and folders |
| cd | Change directory |
| mkdir | Create a new folder |
| touch | Create new files |
| rm | Delete files |
| cat | View the contents of the file |
| pwd | View detailed path of current directory |
| cp | Copy files/folders |
| mv | Move files/folders |
| grep | Find a phrase in files/streams |
| find | Find files and folders |
| vi/nano | File editor (text editor) |
| history | Displays the 50 most commonly used commands |
| clear | Delete the terminal screen |
Use SSH Command.
To use the commands in the SSH command you must log in to the server via SSH through the command line utilities.
On Window 11 you can select PowerShell Windows with the shift + right mouse combination.
Login to SSH with the command:
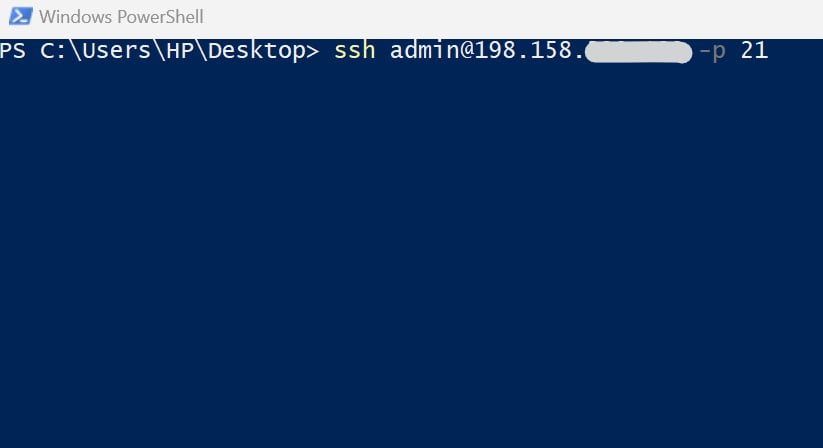
In which user is the login name, severip is the ip of the server, port (if default, leave blank) is the port of the ssh connection.
After entering all of the above information, click Enter. The system will ask for a password and you need to enter the correct password for the SSH connection.
When successfully logged in, the same screen will appear.

Once you successfully log in to SSH, you can use the commands above to perform remote server administration.
GOOD LUCK













